The way forward for identification safety is passwordless, context-aware, and frictionless—and we’re persevering with to construct towards that future at Databricks. We’ve launched new capabilities throughout the Databricks Information Intelligence Platform to assist clients strengthen authentication, automate identification provisioning, and allow safe programmatic entry, making it simpler to implement fashionable, scalable identification and entry controls.
As a reminder, Databricks-managed passwords reached end-of-life on July 10, 2024, and are now not supported within the UI or by way of API authentication. To additional assist a passwordless future, we’re additionally asserting the Normal Availability of Databricks-managed Multi-Issue Authentication (MFA).
As extra clients depend on Databricks to democratize knowledge and AI entry, securing programmatic entry is extra necessary than ever. To scale back long-term API token danger, we’ve launched a number of new controls:
- Computerized revocation of Private Entry Tokens (PATs) which might be inactive for 90 days
- A most lifetime of two years for newly created PATs, so credentials now not persist indefinitely by default
- Normal Availability of the Entry Tokens Report, giving admins deeper visibility into token utilization and danger
These updates align with the course of evolving business requirements, together with NIST, PCI DSS, and ISO, that are shifting away from password complexity towards smarter, extra adaptive identification frameworks.
Right here’s a deeper dive into what’s new and tips on how to take advantage of it.
Simplify your SSO administration with unified login on AWS
We’re transferring all clients to unified login, the place SSO doesn’t must be configured on particular person workspaces. Unified login immediately brings single sign-on (SSO) to all Databricks workspaces in your account.
Unified login allows you to handle one account-level SSO configuration. Meaning much less overhead for admins, constant entry insurance policies for customers, and a stronger general safety posture. Mixed with SSO emergency entry utilizing MFA, unified login additionally offers a safe fallback for directors, guaranteeing centralized management with out sacrificing flexibility.
Unified login is already utilized in 1000’s of manufacturing workspaces, and clients ought to plan their migration to it now. As of December 2024, all new account-level SSO setups are routinely opted into unified login by default. This streamlines rollout and makes it easy for brand new customers to begin utilizing options like AI/BI dashboard sharing, Genie Areas, and Apps with no further configuration wanted. We advocate you progress all workspaces to Unified Login ASAP.

Greatest practices for enabling unified login
To make use of a single account-level SSO setup in your account, guarantee your identification supplier’s (IdP) configuration permits all of your workspace customers to authenticate to the Databricks account. When full, you may confidently decide in any outdated workspaces to reuse account-level SSO with unified login. Lastly, take away outdated workspace-specific IdP tiles to keep away from confusion.
Be safe by default with Databricks-managed multi-factor authentication (MFA)
SSO stays the very best observe for centralized identification administration. Enabling MFA on the Identification Supplier (IdP) aligns together with your firm’s safety insurance policies and ensures a constant, policy-compliant strategy throughout your total consumer base.
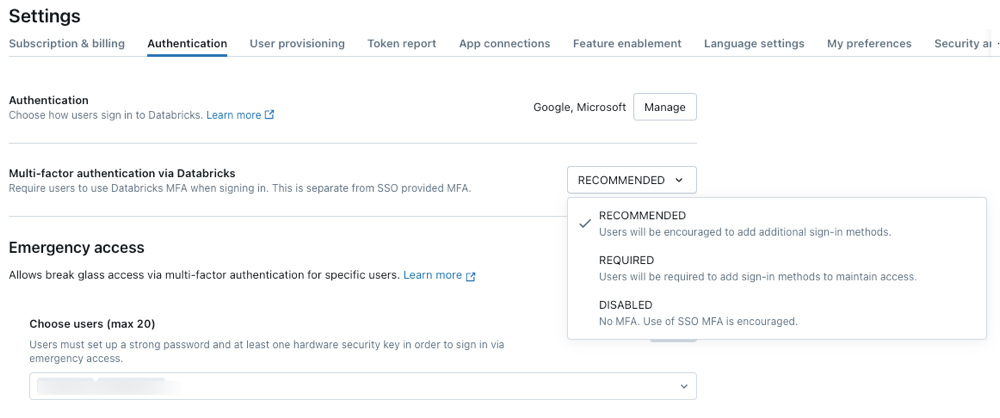
We’re excited to introduce Databricks-managed MFA, now Usually Obtainable for all AWS accounts that haven’t but configured single sign-on (SSO). This new characteristic permits admins to implement multi-factor authentication (MFA) for all customers, enhancing safety throughout your group. With assist for fashionable authenticator apps and passkeys, organising MFA is fast and straightforward. Admins can allow it by the Account Console.
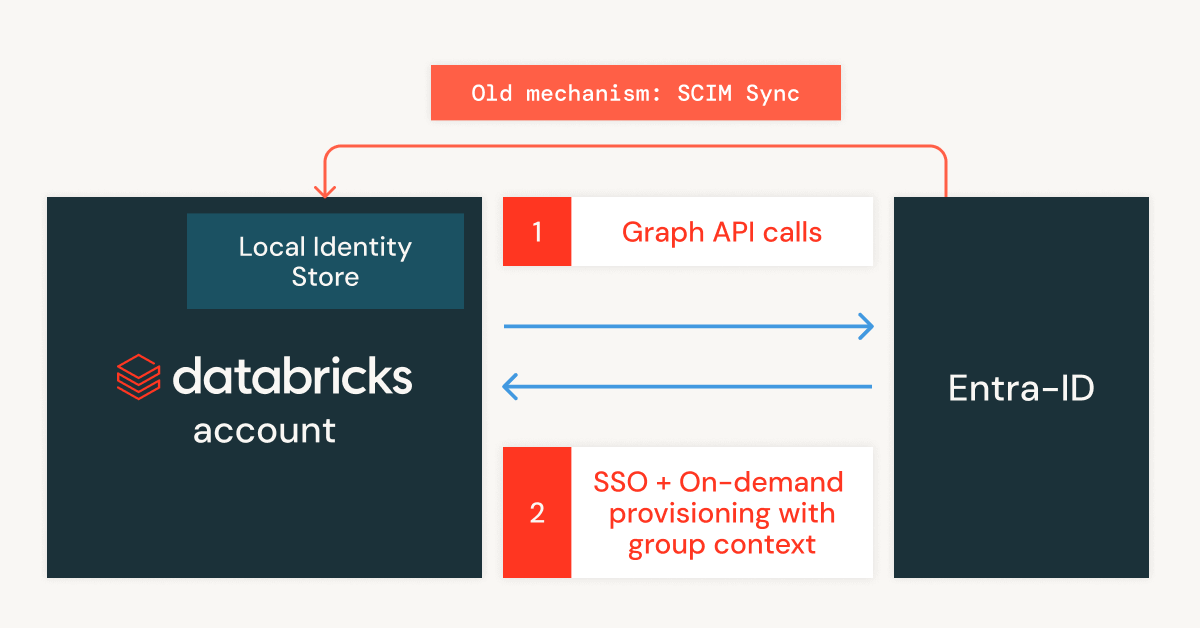
Shortly provision new customers on Azure Databricks with Computerized Identification Administration
Computerized Identification Administration, now in Public Preview for Microsoft Entra ID, allows safe, real-time entry administration by natively integrating with customers, teams, and repair principals in Entra ID, no connector apps or guide sync required. Better of all, it additionally respects nested teams and teams containing service principals, guaranteeing constant entry management throughout advanced identification hierarchies.
Considered one of our key use instances is simplifying the sharing of AI/BI Dashboards or Databricks Apps, the place practitioners can share with any consumer within the group, no matter whether or not they’re in a workspace. This enables dashboard homeowners to share AI/BI dashboards or apps with any Entra ID identification—even these not but in Databricks—for seamless, safe collaboration. New customers are routinely provisioned solely when shared content material is accessed, they usually inherit solely the particular permissions granted, guaranteeing they see and use solely what they’re entitled to. It saves time for admins and makes it simpler for organizations to increase knowledge insights throughout their groups. See our launch weblog for the small print.
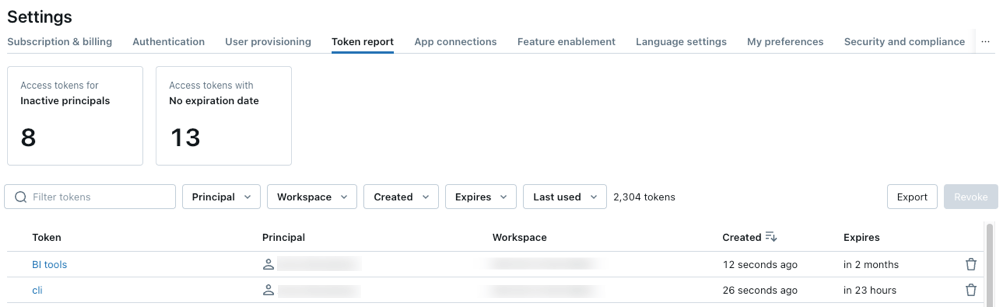
Monitor and handle private entry tokens with new admin instruments
Take management of private entry tokens (PATs) with new token monitoring instruments, now in Public Preview throughout AWS, Azure, and GCP. Whereas we advocate utilizing OAuth entry tokens as a substitute of PATs for improved safety, these monitoring instruments assist scale back danger and enhance entry hygiene by giving admins full visibility into lively PATs, implementing time-to-live (TTL) limits, and enabling fast revocation of compromised or unused tokens.
Admins can now entry this info by a brand new Token Report tab within the Databricks Admin Console. From there, account admins can discover lively tokens belonging to particular customers or workspaces. You should use it to search out older tokens that have been set to by no means expire or these which might be nonetheless lively however haven’t been actively utilized in a month. We particularly advocate searching for private entry tokens belonging to workspace admins and revoking them in the event that they aren’t wanted.
Safe programmatic entry with OAuth Token Federation
To assist clients safe API-based entry, we’re excited to announce added assist for OAuth token federation, which is able to quickly be typically accessible throughout AWS, Azure, and GCP. Token federation permits purposes to authenticate to Databricks utilizing tokens out of your trusted IdP, eliminating the necessity to retailer Databricks secrets and techniques like static tokens or passwords.
You’ll be able to configure token federation at two ranges:
- Account-wide: Allows token federation for all customers and repair principals in your account. For security-conscious organizations that wish to implement constant controls throughout all workloads
- Particular person service principal degree (often known as workload identification federation): For implementing fine-grained management over particular purposes
OAuth Token Federation is very highly effective for patrons managing numerous service principals. For instance, if you happen to’re utilizing 100+ service principals for GitHub Actions, you may migrate them to token federation and eradicate the necessity to retailer and rotate over 100 long-lived Databricks-managed secrets and techniques.
Account admins can configure an account-level federation coverage utilizing the Databricks CLI model 0.239.0 and above, or the Databricks account-wide and service principal token federation REST APIs.
How we strengthen authentication at Databricks
Along with new product capabilities, we lead by instance in our company setting as nicely. At Databricks, along with our centralized single sign-on, we’ve applied:
- {Hardware}-based multi-factor authentication by way of FIDO2 gadgets
- Context-aware authentication that includes gadget belief, geolocation and behavioral patterns
- Automated response to a breached password detection from our menace intelligence sources
- Shifting from quarterly to annual pressured password modifications to encourage higher passwords
- Least privilege dataset-level authorization so {that a} consumer who wants entry to a non-standard desk will be approved for simply that desk as a substitute of a whole different function.
In combination, this offers our staff with easy entry to sources whereas sustaining a powerful safety posture.
Your identification safety modernization journey on Databricks begins right here
Whether or not you’re simply getting began with MFA or able to undertake full automation, Databricks has the instruments and integrations to assist you each step of the best way.
To scale back your safety danger and take full benefit of those capabilities, we advocate the next finest practices:
- Allow SSO on the account degree
- Require MFA for all customers
- Use OAuth federation for API entry
- Monitor authentication logs for uncommon exercise
In the event you’re able to dive in rapidly, our identification finest observe guides on AWS, Azure and GCP are a very good place to begin.
Be a part of the Identification and Entry Administration product and engineering staff on the Information + AI Summit, June 9–12 on the Moscone Middle in San Francisco! Get a primary take a look at the newest improvements in knowledge and AI governance and take a look at our identification and entry administration periods: